Network Packet Broker: Illuminating the Dark Corners of Your Network
2025-08-29
In today's complex, high-speed, and often encrypted network environments, achieving comprehensive visibility is paramount for security, performance monitoring, and compliance. Network Packet Brokers (NPBs) have evolved from simple TAP aggregators into sophisticated, intelligent platforms that are essential for managing the flood of traffic data and ensuring monitoring and security tools operate effectively. Here's a detailed look at their key application scenarios and solutions:
Core Problem NPBs Solve:
Modern networks generate massive volumes of traffic. Connecting critical security and monitoring tools (IDS/IPS, NPM/APM, DLP, forensics) directly to network links (via SPAN ports or TAPs) is inefficient and often infeasible due to:
Tool Overload: Tools get swamped with irrelevant traffic, dropping packets and missing threats.
Tool Inefficiency: Tools waste resources processing duplicate or unnecessary data.
Complex Topology: Distributed networks (Data Centers, Cloud, Branch Offices) make centralized monitoring challenging.
Encryption Blind Spots: Tools cannot inspect encrypted traffic (SSL/TLS) without decryption.
Limited SPAN Resources: SPAN ports consume switch resources and often cannot handle full line-rate traffic.
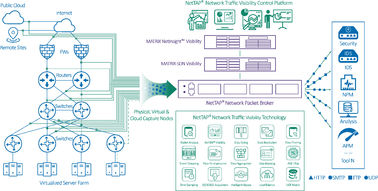
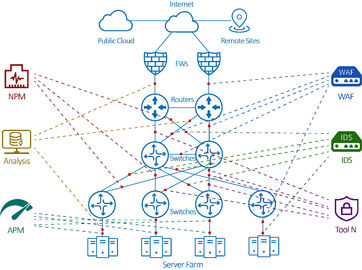
NPB Solution: Intelligent Traffic Mediation
NPBs sit between network TAPs/SPAN ports and the monitoring/security tools. They act as intelligent "traffic cops," performing:
Aggregation: Combine traffic from multiple links (physical, virtual) into consolidated feeds.
Filtering: Selectively forward only relevant traffic to specific tools based on criteria (IP/MAC, VLAN, protocol, port, application).
Load Balancing: Distribute traffic flows evenly across multiple instances of the same tool (e.g., clustered IDS sensors) for scalability and resilience.
Deduplication: Eliminate identical copies of packets captured on redundant links.
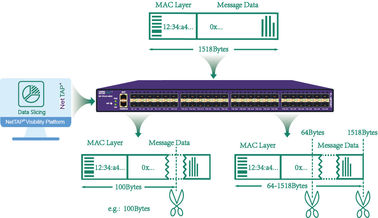
Packet Slicing: Truncate packets (removing payload) while preserving headers, reducing bandwidth to tools that only need metadata.
SSL/TLS Decryption: Terminate encrypted sessions (using keys), presenting clear-text traffic to inspection tools, then re-encrypting.
Replication/Multicasting: Send the same traffic stream to multiple tools simultaneously.
Advanced Processing: Metadata extraction, flow generation, timestamping, masking sensitive data (e.g., PII).
Detailed Application Scenarios & Solutions:
1. Enhancing Security Monitoring (IDS/IPS, NGFW, Threat Intel):
Scenario: Security tools are overwhelmed by high volumes of East-West traffic in the data center, dropping packets and missing lateral movement threats. Encrypted traffic hides malicious payloads.
NPB Solution:
- Aggregate traffic from critical intra-DC links.
- Apply granular filters to send only suspicious traffic segments (e.g., non-standard ports, specific subnets) to the IDS.
- Load balance across a cluster of IDS sensors.
- Perform SSL/TLS decryption and send clear-text traffic to the IDS/Threat Intel platform for deep inspection.
- Deduplicate traffic from redundant paths. Result: Higher threat detection rate, reduced false negatives, optimized IDS resource utilization.
2. Optimizing Performance Monitoring (NPM/APM):
Scenario: Network Performance Monitoring tools struggle to correlate data from hundreds of dispersed links (WAN, branch offices, cloud). Full packet capture for APM is too costly and bandwidth-intensive.
NPB Solution:
- Aggregate traffic from geographically dispersed TAPs/SPANs onto a centralized NPB fabric.
- Filter traffic to send only application-specific flows (e.g., VoIP, critical SaaS) to APM tools.
- Use packet slicing for NPM tools that primarily need flow/transaction timing data (headers), drastically reducing bandwidth consumption.
- Replicate key performance metrics streams to both NPM and APM tools. Result: Holistic, correlated performance view, reduced tool costs, minimized bandwidth overhead.
3. Cloud Visibility (Public/Private/Hybrid):
Scenario: Lack of native TAP access in public clouds (AWS, Azure, GCP). Difficulty capturing and directing virtual machine/container traffic to security and monitoring tools.
NPB Solution:
- Deploy virtual NPBs (vNPBs) within the cloud environment.
- vNPBs tap virtual switch traffic (e.g., via ERSPAN, VPC Traffic Mirroring).
- Filter, aggregate, and load balance East-West and North-South cloud traffic.
- Securely tunnel relevant traffic back to on-premises physical NPBs or cloud-based monitoring tools.
- Integrate with cloud-native visibility services. Result: Consistent security posture and performance monitoring across hybrid environments, overcoming cloud visibility limitations.
4. Data Loss Prevention (DLP) & Compliance:
Scenario: DLP tools need to inspect outbound traffic for sensitive data (PII, PCI) but are inundated with irrelevant internal traffic. Compliance requires monitoring specific regulated data flows.
NPB Solution:
- Filter traffic to send only outbound flows (e.g., destined for the internet or specific partners) to the DLP engine.
- Apply deep packet inspection (DPI) on the NPB to identify flows containing regulated data types and prioritize them for the DLP tool.
- Mask sensitive data (e.g., credit card numbers) within packets before sending to less critical monitoring tools for compliance logging. Result: - - More efficient DLP operation, reduced false positives, streamlined compliance auditing, enhanced data privacy.
5. Network Forensics & Troubleshooting:
Scenario: Diagnosing a complex performance issue or breach requires full packet capture (PCAP) from multiple points over time. Triggering captures manually is slow; storing everything is impractical.
NPB Solution:
- NPBs can buffer traffic continuously (at line rate).
- Configure triggers (e.g., specific error condition, traffic spike, threat alert) on the NPB to automatically capture relevant traffic to a connected packet capture appliance.
- Pre-filter the traffic sent to the capture appliance to store only what's necessary.
- Replicate the critical traffic stream to the capture appliance without impacting production tools. Result: Faster mean-time-to-resolution (MTTR) for outages/breaches, targeted forensic captures, reduced storage costs.
Implementation Considerations & Solutions:
Scalability: Choose NPBs with sufficient port density and throughput (1/10/25/40/100GbE+) to handle current and future traffic. Modular chassis often provide the best scalability. Virtual NPBs scale elastically in the cloud.
Resiliency: Implement redundant NPBs (HA pairs) and redundant paths to tools. Ensure state synchronization in HA setups. Leverage NPB load balancing for tool resilience.
Management & Automation: Centralized management consoles are crucial. Look for APIs (RESTful, NETCONF/YANG) for integration with orchestration platforms (Ansible, Puppet, Chef) and SIEM/SOAR systems for dynamic policy changes based on alerts.
Security: Secure the NPB management interface. Control access rigorously. If decrypting traffic, ensure strict key management policies and secure channels for key transfer. Consider masking sensitive data.
Tool Integration: Ensure the NPB supports the required tool connectivity (physical/virtual interfaces, protocols). Verify compatibility with specific tool requirements.
Network Packet Brokers are no longer optional luxuries; they are fundamental infrastructure components for achieving actionable network visibility in the modern era. By intelligently aggregating, filtering, load balancing, and processing traffic, NPBs empower security and monitoring tools to operate at peak efficiency and effectiveness. They break down visibility silos, overcome the challenges of scale and encryption, and ultimately provide the clarity needed to secure networks, ensure optimal performance, meet compliance mandates, and rapidly resolve issues. Implementing a robust NPB strategy is a critical step towards building a more observable, secure, and resilient network.
Read More

 Your message must be between 20-3,000 characters!
Your message must be between 20-3,000 characters! Please check your E-mail!
Please check your E-mail!  Your message must be between 20-3,000 characters!
Your message must be between 20-3,000 characters! Please check your E-mail!
Please check your E-mail!